
Data Protection Best Practices For Virtual Assistants
Virtual Assistants, or VAs, can perform a wide variety of tasks, and some of them deal with sensitive information. As such, data security is critical for both assistants’ and clients’ best interests. Thus, they must be acquainted with Data Protection Best Practices.
Virtual Assistants, such as those in the Philippines, can handle many VA tasks for businesses, such as the following:
- Administrative work
- Bookkeeping
- Customer support
- Data entry
- Scheduling
- Reporting
However, one aspect that VAs must consider is data security. After all, human error is a leading cause of data breaches. 82% of them are “at least partially caused” by it. VAs should also be familiar with security plans that may help their clients secure their platform, etc.
Here are a few top practices Virtual Assistants can follow to ensure the security of clients’ sensitive information:
Data Protection Best Practices for Virtual Assistants
Install Anti-Virus, Anti-Malware, and Anti-Ransomware Software
Viruses and malware can damage, delete, or steal your files. Meanwhile, ransomware can leave you unable to access your personal data or any specific files unless you pay a ransom.
Thus, Virtual Assistants and businesses must educate themselves on the different types of viruses. Organizations should also install anti-virus, anti-malware, and anti-ransomware software on their VAs’ devices.
In addition, VAs must also learn the risks of the following:
- Downloading and installing software from untrusted sources;
- Downloading email attachments from unknown sources, and
- Clicking on suspicious links.
After all, security software prevents, detects, and mitigates threats to data security. Complacency in data protection leads to breaches or other security incidents. So, VAs and organizations should choose and install the best software that fits their requirements.
Use Widely-Accepted Security Measures
To ensure security, Virtual Assistants must follow Data Protection Best Practices. Here are some key security measures that can help protect sensitive information:
- User Authentication. Authentication mechanisms can ensure that sensitive data is only accessible to authorized users like the Virtual Assistant. Some examples of this measure include Two-Factor Authentication and access control or restricting access to the VA’s data and systems to authorized personnel only.
- Data Encryption. Data transferred and saved between the user and the Virtual Assistant must be encrypted using various protocols. A dedicated security team can encrypt the data on your Virtual Assistant’s devices to protect against eavesdropping and data breaches.
- Anonymization. You can anonymize data to prevent it from being traced to a particular user.
- Data Minimization. You must collect the data necessary to fulfill a user’s request and discard it upon completion. So, you must avoid storing unnecessary personal information.
- Implementing Intrusion Detection Systems. Firewalls and intrusion detection systems monitor and filter network traffic. They identify and block potentially malicious activities.
- Do Regular Updates. Keep the Virtual Assistant’s software or devices updated with security patches and updates.
Enable Two-Factor Authentication or 2FA
Single-Factor Authentication (SFA) methods were once the norm and still are in some cases. However, using Two-Factor Authentication is preferred instead.
Signing up for a new website or a subscription service means creating a unique username and password. So, a user account’s security depends on a password’s strength.
Thus, users are discouraged from using the same password across multiple platforms. However, they continue to do so to avoid forgetting them.
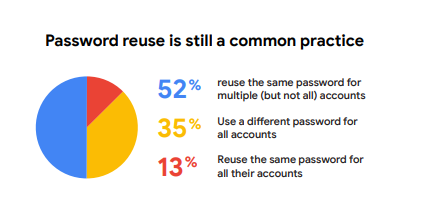
Source: Google.
Contrary to SFA, Two-Factor Authentication presents an additional security layer. With 2FA, it’s more difficult to access your account to prevent data breaches.
For instance, you can log into an account on a desktop by requesting a Time-based One-Time Password. You can only successfully log in once you input the right verification code sent to your mobile device. Another form of 2FA involves facial or fingerprint scans.
User Education on Data Privacy Best Practices
You must inform Virtual Assistants about data policies and request consent. In particular, organizations must prioritize consent and transparency regarding data collection and usage policies. Additionally, privacy policies should be easily accessible and understandable to VAs.
User training on Data Privacy Best Practices is also essential. For example, teaching your VAs not to share sensitive information and setting strong, unique passwords reduces the risk of data breaches or leaks.
Organizations ensure they safely and responsibly handle data by empowering assistants with knowledge and resources. Thus, educating VAs on how to secure data handling is critical.
Establish a Data Breach Protocol
With the amount of sensitive information Virtual Assistants handle, they avoid data breaches at all costs. Of course, they must only process their data while understanding that they don’t fully control it.
While data breaches aren’t welcome nor expected, it’s still best to establish a concrete protocol for addressing them if they come up.
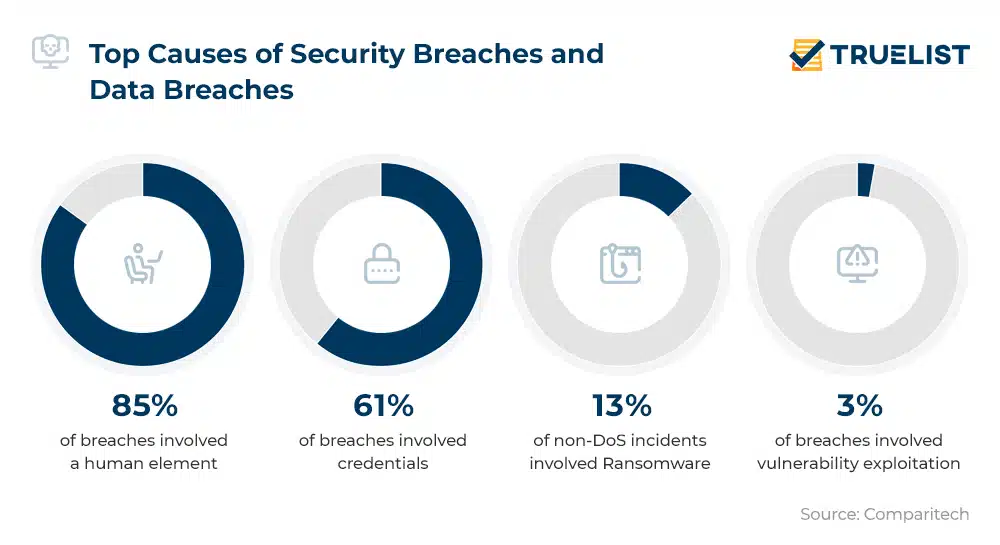
Source: TrueList.
When experiencing a data breach, your priority should be immediately ending it. But what comes next? You need a well-defined data breach response plan, including notifying stakeholders, the appropriate regulatory authorities, and the public if necessary.
Therefore, you should consult with your VAs on the steps to protecting sensitive data in the future.
Use Trustworthy Cloud Services
You must choose a trusted, safe, and secure cloud backup platform. After all, if you use third-party services — Cloud Based Software or otherwise — you must carefully assess their data protection practices. Always select the services that meet your organization’s standards.
For example, some software programs allow Virtual Assistants to store data online. Thus, they reduce the need for physical documents, which may be easily lost. On the other hand, when VAs get rid of unnecessary data, they must remember to check the files and media stored online.
After all, data protection also involves knowing how to properly dispose of data on your cloud backup service. It’s as essential as overwriting data on your local drives and physically destroying hardware.
Secure the VA’s Phones or Mobile Devices
Data protection for mobile devices is easily overlooked when focusing on securing a Virtual Assistant’s computer and its connections.
VAs’ phones can also contain sensitive information, such as messages with clients and call logs. In addition to minimizing the amount of data a VA stores on their mobile devices, an organization should also be critical of the wireless networks their assistant is connected to.
Install a Password Manager
Virtual Assistants can also utilize a password manager such as Dashlane or 1Password as an alternative precautionary measure to protect data. This way, they no longer have to reuse passwords or memorize every single one.
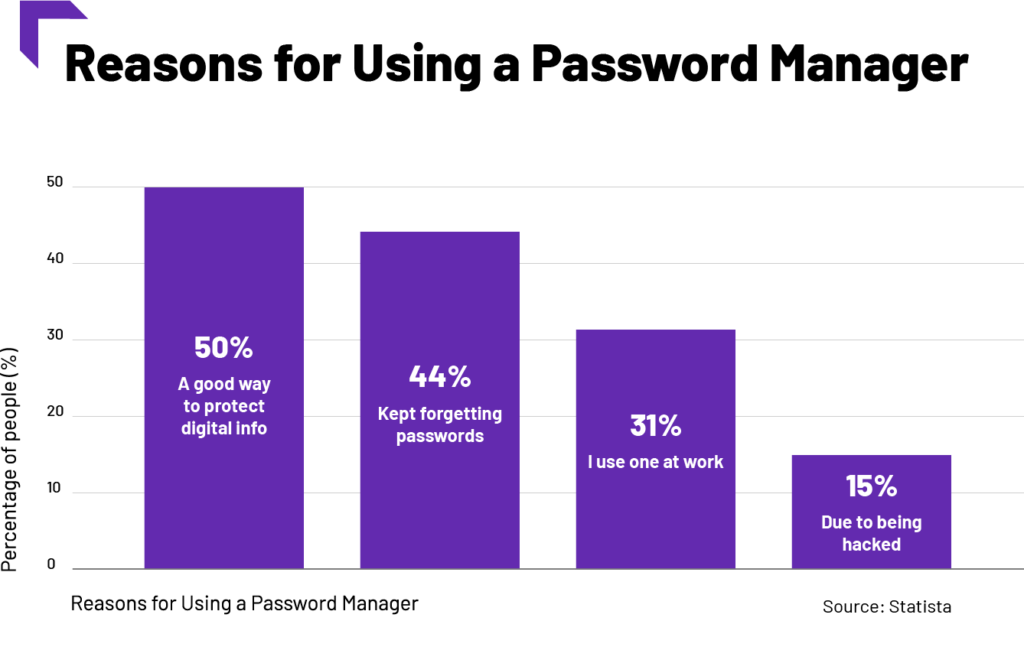
Source: Tech.co.
Instead, whenever a VA needs to log into any account, they can simply input a master password into the password manager. Then, the program logs you on the corresponding website.
Also, depending on the software you use, your VA may gain additional security layers. These include features such as the following:
- Encryption and decryption processes;
- Analytics for password strengths;
- Automatic password changers, etc.
Final Thoughts
To secure sensitive information, Virtual Assistants shouldn’t limit themselves to certain data protection methods only. There will always be room for improvement and new knowledge, so have your VAs utilize data protection practices and methods today!
Virtual Assistants in the Philippines make it a part of their responsibility to get more information and details about data security. For instance, they must learn more about the General Data Protection Regulation or GDPR. Remember to include similar and complementary laws regarding data protection in your country as well!
Here are other ways VAs protect data:
- Limit file sharing.
- Read through the privacy policies of any services you may be using.
- Look at reviews on any new software for Virtual Assistants, especially those you intend to use.
- Thoroughly evaluate updates from your operating system, software, website, themes, or plugins.
Data protection measures for VAs also depend on the types of data they deal with and how frequently they work with them. It’s best to assess the VA’s work system, processes, and protocols first. Then, structure your data protection strategy around what works best for you.













Comment 0